First of all, the best thing you can do to isolate hotspot users from your existing network, is to put the hotspot router directly to the internet connection (first router in your network). Then connect other routers to the hotspot router. That way, the hotspot users won’t see other part of your network.
Furthermore, there are several tricks you can do based on your hardware/firmware you are using:
(Note that if you have a local DNS on the restricted subnet, then the hotspot will not work. )
Suggested setup is to put the dd-wrt hotspot router as the first router on your network (connected to an ADLS modem for example), then connect the hotspot router to your office router. That way, hotspot users won’t be able to see your office network.
To restrict access to your office network from the hotspot’s subnet you need to edit a file in the router via SSH (using putty.exe or ‘ssh {IP ADDRESS OF YOUR ROUTER}’ from a terminal on MAC).
If you logged in please type:
vi /etc/chilli/ipup.sh
It’s a blank file yet, so we are going to add an iptables (firewall configuration) command:
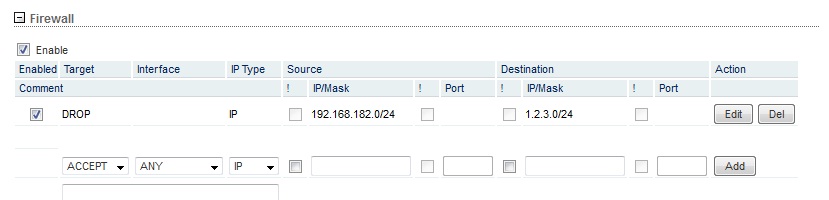
iptables -I FORWARD -s 192.168.182.0/24 -d 1.2.3.0/24 -j DROP
where 192.168.182.0/24 is the hotspot subnet and 1.2.3.0/24 is your office subnet, this sets he firewall to drop all packets from your hotspot network to your office network.
If you’re done, press Esc and type :x, then hit ENTER to save the file.
You can type ‘reboot‘, to reboot the router.
You can either select the “Isolate WLAN clients” under the Network/advanced wireless settings -this will protect hotspot users from sharing their laptop files with others
or select deny for “Hotspot LAN Access” on the Hotspot/configuration page so that hotspot users will not be able to access the regular LAN.

Hello,
it´s possible to block the Hotspotsystem from the Local Network.
In DD-WRT i made the following Settings:
Go in the Admin / Diagnose-Tab and set the Following IPTABLES-Rules in the Windows and then
“Save as Firewall” – It works perfect on my Routers. Nobody have Access to Local Network and the Admin-Page.
Normally You don´t need the DROP-Lines for telnet, ssh, www and https, because the 192.168.0.0/16 Drops it all,
so the Access to other Hotspot-User in the 192.168.182.0/24-Network is blocked too. But Secure is secure 😉
#——————————————————————————————
## ISOLATION HOTSPOTSYSTEM FROM LOCAL NETWORK
iptables -A FORWARD -i tun0 -j DROP
#Blocking Access to Local Network from Tunneling-Adapter
iptables -t nat -I PREROUTING -i tun0 -d `nvram get lan_ipaddr`/`nvram get lan_netmask` -j DROP
# Blocks Access to the typically “Private IP-Adress-Range” (You can set more Lines with additional IP-Ranges)
iptables -t nat -I PREROUTING -i tun0 -d 192.168.0.0/16 -j DROP
# Blocks Access to the Router from the Hotspotsystem IP-Range, exect 3990 (Radius, Important for Logon and Logoff)
iptables -t nat -I PREROUTING -i tun0 -d 192.168.182.1/32 -p tcp –dport telnet -j DROP
iptables -t nat -I PREROUTING -i tun0 -d 192.168.182.1/32 -p tcp –dport ssh -j DROP
iptables -t nat -I PREROUTING -i tun0 -d 192.168.182.1/32 -p tcp –dport www -j DROP
iptables -t nat -I PREROUTING -i tun0 -d 192.168.182.1/32 -p tcp –dport https -j DROP
iptables -t nat -I PREROUTING -i tun0 -d 192.168.182.1/32 -p tcp –dport 3990 -j ACCEPT